IT & Engineering
What are SYN flood attacks and how can you defend against them?
SYN flood attacks are one of the most common types of cyberattacks targeting organizations today. They are designed to overwhelm your network’s resources with malicious traffic, leading to a total system shutdown. How do you stop it? We’ve got all the resources you need to survive this flood.
PUBLISHED ON
“We’re under attack!” It’s a line that could very well be taken directly from Star Wars or The Matrix, but it’s also a cyber security reality. These attacks are not only sneaky but can be incredibly sophisticated and engineered to target your specific infrastructure.
SYN (synchronization) flood attacks are definitely in the sophisticated attack category and difficult to defend against, it is important to understand how they work and how to keep your networks protected. Keep reading to explore what SYN floods are, how they work, and how you can defend your organization.
Table of content
Here’s our short list of key things to monitor:
Firewalls and load balancers
Rate limiting
Lower SYN retries
SYN cookies
Honeypots & honeynets
What is a SYN flood attack?
A SYN flood attack is a type of cyberattack that targets a computer network, usually with the goal of disrupting service. It sounds apocalyptic, but it generally isn't designed to disable your entire service. To understand how a SYN flood attack works you need to understand a little about how servers handle incoming connections.
SYN flood attacks are one of the most common types of Distributed Denial of Service (DDoS) attacks, and it works by taking advantage of the standard three-way handshake protocol used in Transmission Control Protocol (TCP).
When a normal client wishes to initiate a connection, it sends a SYN packet to a remote server. The server records the SYN request in a queue, and then a response called a SYN/ACK is sent back to the IP address of the client. When under attack, the hacker (client) sends multiple SYN packets to a server using fake IPs. Because the IPs aren’t genuine, the server isn’t able to respond and becomes overwhelmed, impacting its ability to communicate with legitimate requests.
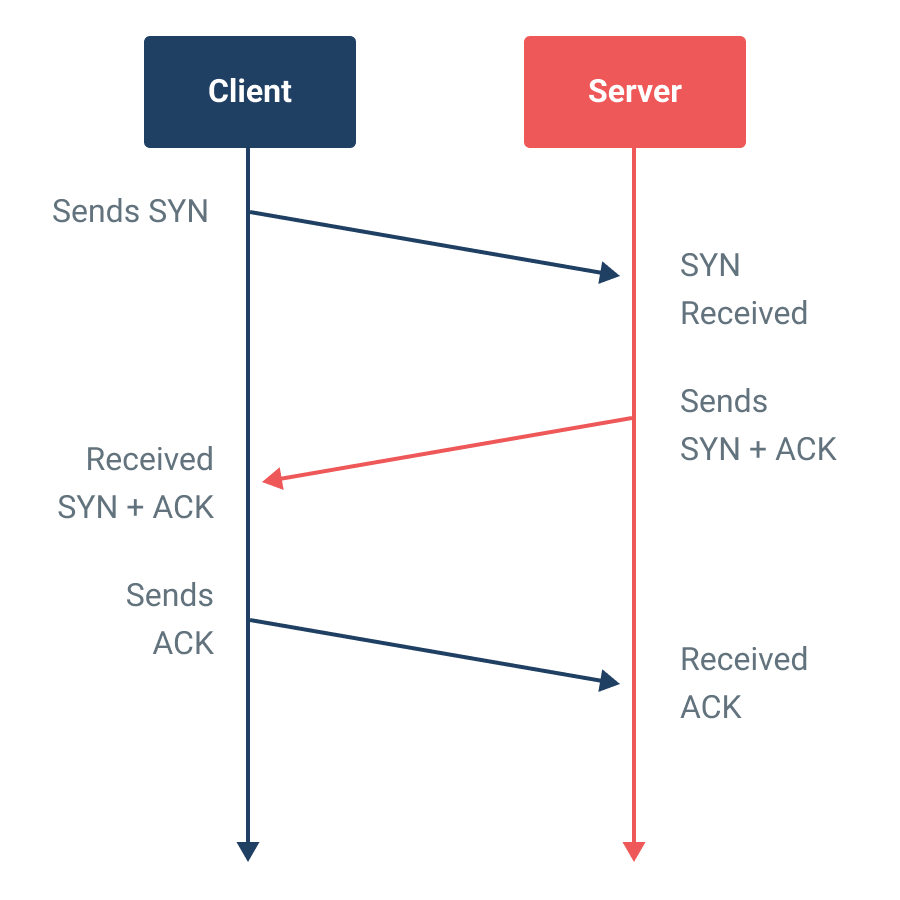
Process of a normal connection between a client and server.
How does a SYN flood attack work?
Attacks like this can happen without warning and can be hard to detect (we said they were sneaky), so it helps to know how they work.
Step one: The attacker sends multiple SYN packets, or requests, to a server that has been configured to respond to each request with ACK.
Step two: The attacker then spoofs the IP address of these requests so that the responses go nowhere, and the target system cannot respond.
This is how a SYN flood attack exploits the SYN queue and floods the server with SYN packets. The attacker has no intention of ever responding to SYN/ACK packets sent by the server. When the SYN queue is full, we say that it overflows and as a result the server drops the SYN request and never responds to the client with a SYN/ACK.
The goal of this type of attack is simple: overwhelm a system's resources with malicious traffic and cause a complete shutdown or disruption. The fastest way to do this is to send a large number of SYN packets to the target machine simultaneously, consuming all its available resources. This makes the system unusable. In some cases, attackers may also use other methods such as flooding algorithms or packet fragmentation to further disrupt service.
What are signs of a SYN flood attack?
Increase load on your servers can be a sign of a SYN flood or other DDoS attack but not all server spikes are attacks. The internet is a weird place, and with viral social media incubators around, it’s possible that significant traffic spikes are totally legit. So, how do you tell malicious spikes apart from genuine ones, and what are some of the signs you should monitor for? We talked to our Mailgun pros to steal their expertise.
Given the way a SYN flood attack is designed to exploit the TCP handshake process to overwhelm infrastructure with a flood of SYN requests, your infrastructure can become overwhelmed and actual legitimate requests will fail to be serviced. The best way to handle a SYN flood is to make sure you're able to detect one if it's occurring and to make sure you're as prepared as possible to mitigate the attack traffic.
Zachary Deptawa, Site Reliability Engineer at Sinch Mailgun
To identify and protect against a SYN flood attack, monitoring is key. You’re looking for any sudden spikes in traffic or changes in traffic patterns. SYN flood attacks trigger servers to send SYN/ACK packets in response to each SYN request sent with the attack. In a typical cycle, these responses are returned to the client, but by design, an attack strategy may be to spoof the return addresses to other well-known IP addresses across the internet.
Server logs should be checked regularly for any suspicious activity, while port scanners should be used to detect open ports that may be vulnerable. Additionally, organizations should analyze the network for malicious IP addresses that could be used as part of an attack.
Here’s our short list of key things to monitor:
Increased inbound network traffic: A SYN flood attack generates a very large amount of network traffic, which will result in a significant increase in the number of incoming connections.
Slow network performance: The increased traffic can cause the network to slow down, resulting in slow response times for legitimate users.
Flooded SYN queues: Keep an eye on the count of connections stuck in the SYN queue. If the queue is filling and connections are not being accepted, that's a good indicator that something fishy is going on.
Unresponsive servers: If the requests make it to the SYN queue on backend servers, they can be overwhelmed by the flood of SYN requests. The servers may then become unresponsive and unable to handle any requests.
How to prevent a SYN flood attack
Aside from regular monitoring, you can set yourself up to prevent SYN flood attacks by installing an Intrusion prevention system, configuring your firewall, installing up to date networking equipment, and using commercial monitoring tools.
Firewalls and load balancers
Certain types of load balancers and other networking gear are built to handle the entire TCP SYN/SYN-ACK/ACK handshake and are able to shed SYN flooding before it can impact your backend servers.
You can still feel the impact of a SYN flood attack even with networking gear built to help mitigate it, but having the load off of your backend infrastructure helps limit the impact.
Rate limiting
Rate limiting is also an important tool for preventing a SYN flood attack. Rate limiting intentionally limits the number of requests a server receives from each individual IP address over a certain amount of time. Setting connection limits for incoming traffic can help prevent a flood of SYN requests from overwhelming the server.
Lower SYN retries
If you have SYN retries enabled and SYN flood traffic impacts your servers, they will attempt to retry the handshake N number of times (N being whatever the retry count is set to). Should an attacker be spoofing IP addresses, it could cause a reflection attack that could get your public IPs on an abuse list. SYN retries being enabled is normal, but make sure the count is not too high - this setting will be specific to your own environment but is something to consider tuning if possible.
SYN cookies
Using SYN cookies is another useful strategy to prevent these attacks. SYN cookies are an attack mitigation technique that can help mitigate the impact of a SYN flood attack by allowing the server to respond to legitimate requests while ignoring the flood of SYN requests.
Honeypots & honeynets
Implementing honeypots or honeynets can also help prevent SYN floods. These tools can also help divert attackers away from critical resources. A honeypot is a decoy. It’s a single computer or service that lives on your network and it works to attract attackers like flies. A honeynet works on the same principle, but instead of trapping attackers it studies and learns their behavior across a series of planted honeypots.
Although there is no absolute solution for protection against this type of attack, having multiple layers of defense will minimize the chances of becoming a victim. This starts with your architecture.
Final thoughts
Despite their effectiveness, SYN flood attacks alone are not enough to completely bring down an entire system. However, when combined with other techniques such as flooding the target's resources or using malware, these attacks can be used to significantly weaken your security posture.
All of these recommendations will vary based on your environment, traffic patterns, and requirements, The best protection against DDoS attacks, SYN flood attacks, and other variations is knowledge. We’ve gained our expertise through experience. Want to level up? Make sure to subscribe to our newsletter and we’ll share all we know.
Keep me posted! Get our news and tips every week.
Popular posts

Here’s everything you need to know about DNS blocklists
The word “blocklist” can almost seem like something out of a movie – a little dramatic, silly, and a little unreal. Unfortunately, in the real world, blocklists are definitely something you...
Read more


