Product
Security matters: Say hello to two-factor authentication (2FA)
Product

It’s that kind of Monday: You show up to work, and you’ve been logged out of your Mailgun account. You input your password, and it prompts you to enter a verification code sent via SMS to your phone.
Please input the six-digit code we sent to +1 (xxx) – xxx – 8318 to access your account.
Welcome to two-factor authentication, or 2FA for short. In this article, we’ll go over what 2FA is, different authentication factors, and types of 2FA. Then we’ll cover how to use two-factor authentication in your daily cybersecurity practices and what to do if you need help with 2FA.
2FA is a security system that requires two independent forms of identification to gain access to an account. This is useful for both account security and account recovery. Usually, the first form of security is your password to the account. The extra layer of security can rely on one of the following:
There are other methods, but these are the most common. The unique password or token is sent via email or text message to another trusted device, account, or phone number, and is required every time you attempt to log into your account. Anyone logging into your account will need to know your super-secret password AND access your 2FA code.
2FA increases the security of your account and guards against cybersecurity threats like phishing, key-logging, and other attacks by hackers. After all, you don’t want to send spam to your consumers after being hacked. 2FA is just as important for you as a developer as it is for your users.
According to an Insurance Information Institute report, consumers reported losing more than $3.3 billion to fraud in 2020. As cybersecurity threats become more prevalent, businesses are responsible for providing stringent account security for their websites and mobile apps.
2FA relies on two separate authentication factors to verify your identity and grant you access to your account.
Authentication factors are different categories of security credentials that can verify a user’s identity and authorize access to a secured account. The most reliable authentication factors are:
Now that we know the different authentication factors, let’s look at some types of 2FA which employ the above factors.
We’ll look at:
Hardware tokens are physical tokens, like a key fob or USB stick, that generate a new numeric code every 30 seconds or so. These tokens either display the code the user must manually input into their login page, or plug directly into a device’s USB port.
The downside to hardware tokens is that they’re easy to lose and are costly for businesses to replace.
SMS codes are a common form of 2FA. The example at the beginning of this article is an example of an SMS verification code. Once the user tries to log into their account, they’re redirected to a second device where they receive a code to input on the login page to gain access to their account. In most cases, the primary device the user is logging in from is a laptop or desktop computer, and the second device is a mobile phone. Of course, there are variations on this if the user uses voice over internet protocol (VOIP) solutions like Google Voice.
Instead of sending the user a password or code, the website or application can simply send a push notification to an app notifying the user that a login attempt is happening. Then, the user can confirm or deny the login attempt to grant or restrict access.
Software tokens, like TOTP, are one-time use, software-generated passcodes. First, the user must download and install a 2FA app on their computer, tablet, or smartphone. When they go to log into their account, they’ll be prompted to enter a software token generated on their 2FA app. These tokens are similar to hardware tokens in that they expire about every 30-60 seconds.
How you use 2FA differs depending on the web service. At Mailgun, our 2FA process requires the use of an authenticator app.
IMPORTANT: Before we dive into our 2FA process, we want to highlight the importance of step 5 below. When activating 2FA for your Mailgun account, you’ll see your account’s “paper key.” This key grants you access to the account if your authenticator app or device is no longer working. Keep this key safe – it’s shown only once and can’t be generated again. Not even our Mailgun team can retrieve your paper key for you.
Without further ado, here’s the process for using 2FA with your Mailgun account:
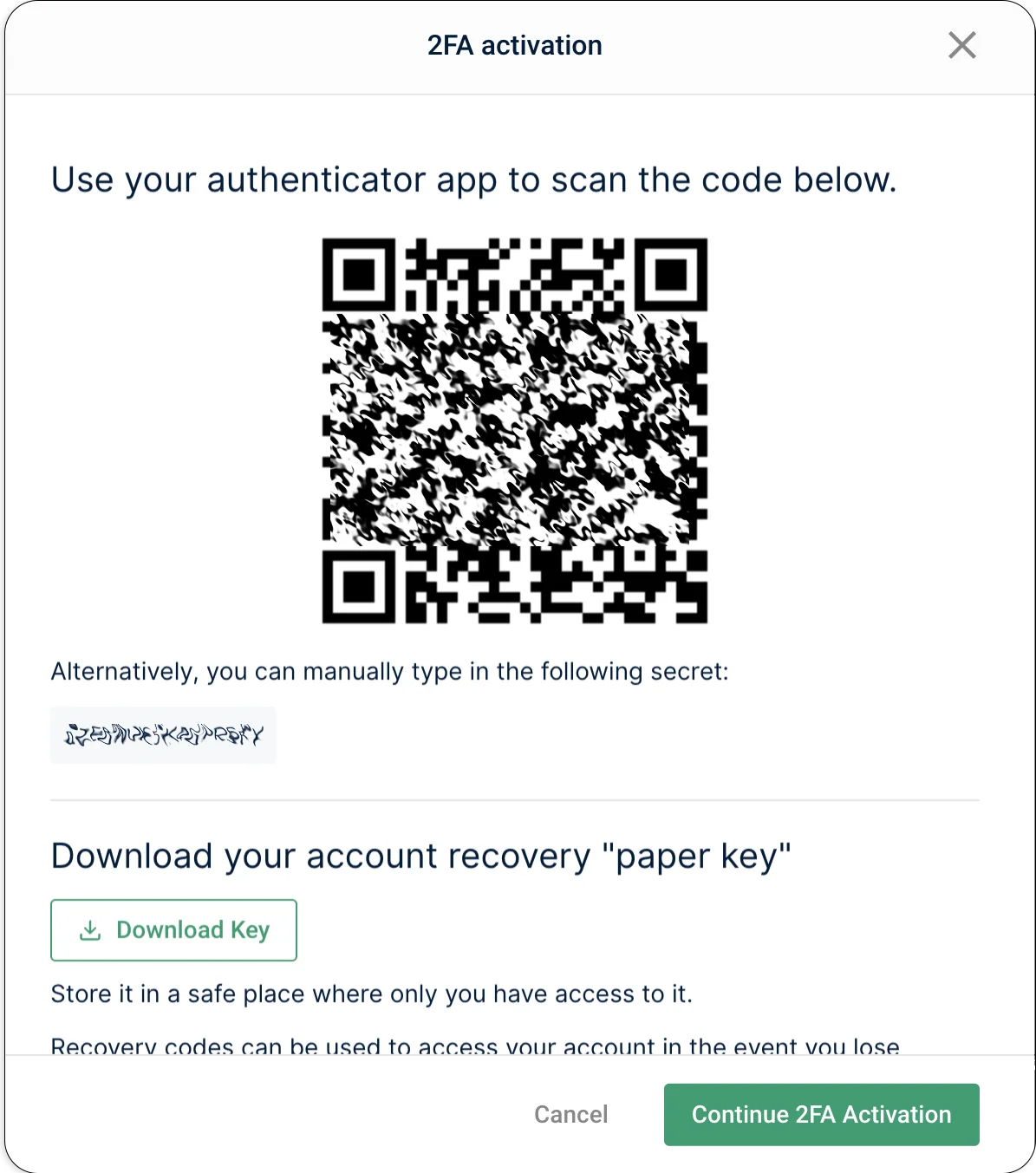
If you ever need help using 2FA with your Mailgun account, don’t hesitate to reach out to the Mailgun Support team. We’ll sort things out.
Keep in mind your paper key can help you authenticate if your app is no longer working.
And that’s it! Use 2FA to keep your account extra secure. After all, your account is only as strong as your weakest access point. In fact, if you have a multi-user account with Mailgun, we recommend taking advantage of Mailgun’s user roles. On the off chance that your account ever gets compromised, this article can help.
Keep your keys close and out of prying eyes, your passwords complex, and your management team from firing you. Opt into 2FA to keep your accounts yours!
Is 2FA one of your security requirements? At Mailgun we stay on top of security and compliance standards. Learn more here about setting up an account and sending securely.
Want more security tips and email know-how? Don’t forget to subscribe to our newsletter so you never miss a beat.
Send me the Mailjet Newsletter. I expressly agree to receive the newsletter and know that I can easily unsubscribe at any time.