Key rotation best practices: Keeping your email program secure

Hey, what’s your password?
Many of us have been managing passwords for decades. Maybe it started with your Neopets account, but somewhere in the early 90s, password protection joined the conversation and never left.
Since then, security has evolved in an intricate way, and every app, platform, and tool each has their own protocols. On top of basic authentication, many other security authentications have been built over the years, and email is no exception. In terms of keeping prying eyes and malicious hackers away from your email program, we’ll focus on the importance of protection for your DKIM and API keys.
In this post, we’ll talk about the undeniable importance of key rotation, how often to cycle credentials and how to secure your email program if your credentials are leaked on platforms like GitHub.
There are few things that can send your heart plummeting into your stomach the way a security breach can. It’s instant panic.
Why? With the way systems are interconnected, even a single employee password can expose incredible amounts of sensitive data; user data as well as company data and additional credentials like API keys and DKIM keys.
Key rotation is the process of periodically changing the credentials protecting your resource to reduce the risk of unauthorized access.
Just like runners, keys can become exhausted. Key exhaustion occurs when keys are used beyond their authorized lifespan. Your company may have time limits for keys to protect against exposure, but also to keep them from being encrypted with too much content.
When we talk technology, keys exist everywhere. When we talk about your email program, keys exist within your email authentication protocols, and in the APIs that connect your services and automate your sending. Let’s talk about the two most important types of keys to email.
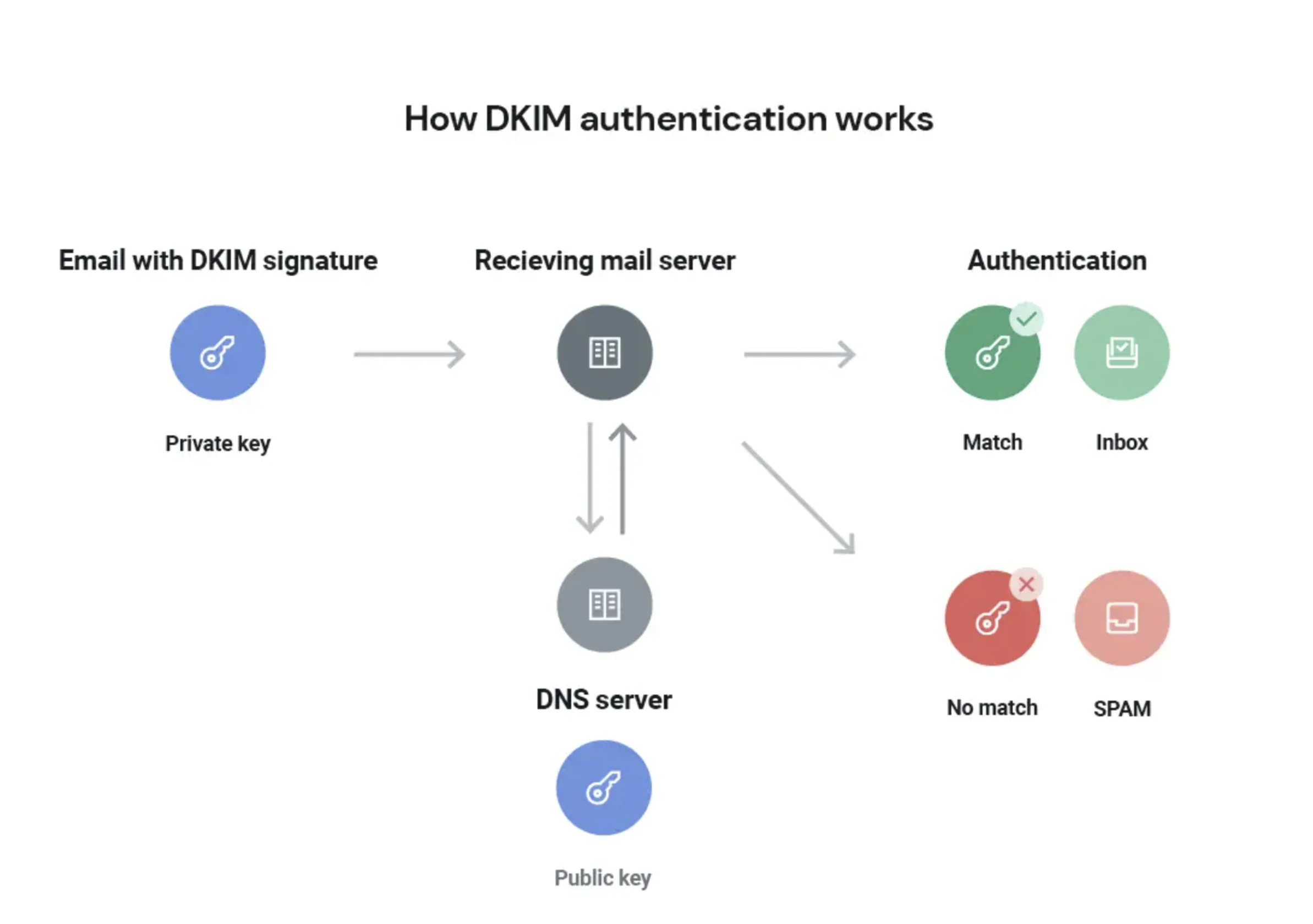
First off, what is DKIM?
DomainKeys Identified Mail (DKIM) is a protocol that email recipients use to verify your sender identity. This is done with two keys:
This validation supports your sender reputation by protecting your recipients from malware and phishing attempts.
If hackers and spammers get a hold of your DKIM credentials, they can spoof your domain. As a sender, leaked DKIM keys aren’t just bad for your reputation but – if you use a shared IP as many senders do – it’s bad for the reputation of anyone sending with from that shared IP addresses, as well as any linked sub-IPs. The result is a rapid decrease in email deliverability for everyone involved and recovery is not an easy process.
One attack done using exposed DKIM keys is the replay attack. The purpose of the replay attack is for a bad actor to leverage a good sender’s reputation for their spam or malicious content.
In a replay attack, a bad actor creates a message with an exposed DKIM signature. Once the signature is added, the message can be resent, or “replayed” over and over to a high volume of recipients. If the message content doesn’t change, the signature will still be validated by the receiving mail server.
DKIM key rotation limits the exposure these bad actors gain to your reputation by cycling the key credentials so they are not able to validate their messages.
DKIM verifies the authenticity of emails and prevents spoofing. To ensure effective DKIM implementation, here are some best practices:
But implementing DKIM isn’t enough. Just like any other credentials, DKIM keys should be rotated periodically to maintain security.
Set a schedule to update your DKIM keys at regular intervals, such as every few months or as recommended by your email service provider. At Mailgun, we recommend rotating DKIM keys every 6 months.
To do so, ….
Stay vigilant by monitoring the DKIM authentication status of your outgoing emails.
Regularly check reports and logs provided by your email service provider to detect any anomalies or potential vulnerabilities.
APIs connect two software components together and allow them to communicate. The way that APIs can communicate with one another are defined by the writers of the API through definitions and protocols. You can have an API that fetches your daily news, build one that retrieves cat photos and cocktail recipes for you on the internet, or – more to the point – use an email API to manage and automate large-volume sending.
APIs are protected by API keys made up of a string of generated characters. Keys are used to link software components and apps together so the APIs can exchange the required data.
Without the correct API key, no communication is possible. But if you have the keys to the API kingdom, you can manipulate a lot of information, steal email lists, pull segmentation data, grab user demographics, etc.
When API keys get exposed, it can become headline news, and it happens more often than you think. Anything from a screenshot posted in a blog, to sending credentials through unencrypted channels, to hardcoding in some source code that gets pushed to GitHub.
When managing API keys, consider the following best practices.
Store API keys securely with an encrypted storage solution or password manager. Don’t hardcode keys within your source code or public repos, and don’t leave your laptop unattended in a public space.
By combining regular DKIM rotation with other security measures like IP allowlisting and role-based access control (RBAC) for API keys, you can significantly enhance the overall security of your email infrastructure.
Apart from key rotation, general password health is as important as dental hygiene in today’s world. Instead of brushing twice daily, use unique passwords and encrypted storage. Instead of flossing, implement tools like 2FA and educate your team on password protection and phishing scams.
Create complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. Not feeling very creative? That’s OK – use a password generator to help you manage password creation.
As a best practice, avoid reusing passwords across different platforms and use encryption and secure storage to save all your credentials.
Enable 2FA whenever possible to add an extra layer of security to your accounts. This authentication method requires users to provide a second verification factor, typically through a code sent to their mobile device.
Always remember that passwords are meant to protect from bad actors, but bad actors can be crafty.
Phishing attacks are extremely common, and one tactic is to use spoofed emails that mimic fellow employees or senior leadership, asking you to share a password or click a link and enter authentication like in this fake Mailgun website. These attacks can be sophisticated, so your security game should be too.
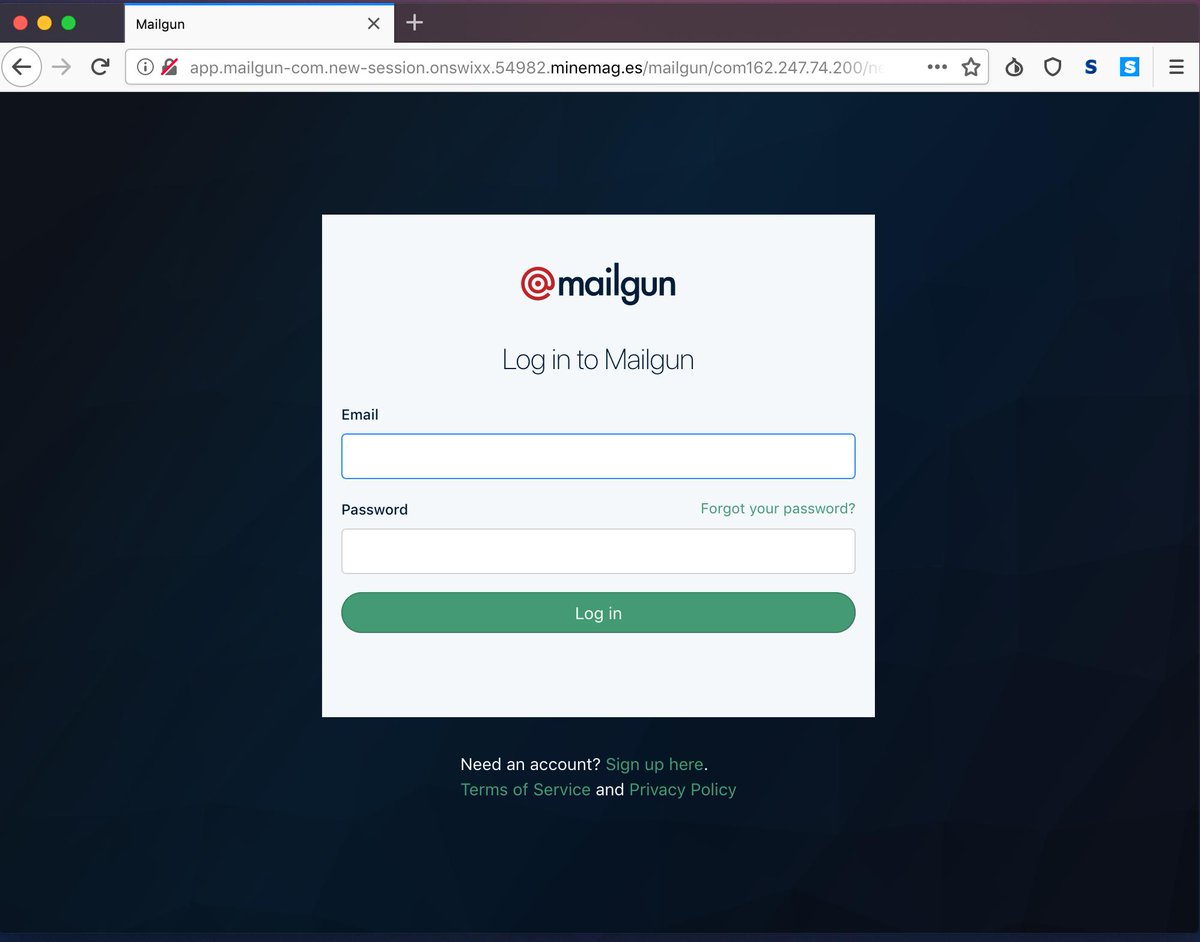
Phishing attacks prove the importance of password security, but also validate key rotation. It would be a lot harder for spammers to send these phishing emails if DKIM key management was more widespread.
Key rotation is an essential practice to mitigate the impact of leaked credentials and improve the security of your email program and other applications. By following best practices for DKIM, API key management, and general password security, you can significantly reduce the risk of unauthorized access.
Preserve your reputation and safeguard sensitive information by adopting these key rotation best practices. Stay proactive and vigilant in the face of evolving cyber threats by using a platform like Mailgun that helps you manage your authentications.