Deliverability
Understanding Yahoo sender requirements: Insights from Yahoo’s Marcel Becker
Deliverability

Marcel Becker, Sr. Director of Product Management at Yahoo, joined our podcast, Email’s Not Dead, to share his insights on the Yahoo inbox requirements and shed light on why these changes are happening now, and what these updates mean for the relationship between senders and mailbox providers.
ESPs (us included) have been shouting about these inbox requirements since they were first announced in October 2023. To recap, Yahoo and Gmail both are enforcing updates that will require senders to abide by these key standards:
These requirements are both industry-shifting, but also kinda not. We’ll get into it more below, but having an unsubscribe process, and maintaining low spam complaint rates were already part of the standard best practices recommended by mailbox providers and ESPs alike.
The most significant of these requirements is arguably authentication – particularly the adoption of DMARC which has previously been an optional authentication for bulk senders. But as we break down these requirements it’s important to know that nothing is really changing in terms of how mailbox providers handle and treat email. It’s just being more clearly defined, more strongly enforced, and more publicly talked about.
“We can sum up the pending updates real quick. It’s going to be three changes, authentication, authentication, authentication.”

Listen to the full podcast episode on Email’s Not Dead
Let’s start with who these requirements affect. The updates impact bulk senders, but what is a bulk sender? For these updates, a bulk sender is defined by Google as a sender that sends 5,000 or more promotional messages in a day. Yahoo has intentionally stayed away from putting a number to the bulk sender definition as the reality is that 5,000 is more of a guidepost than an iron nail.
“The number is not 5,000, or 6,000, or 4,000. If you send 4,999 messages, you still have to follow the requirements. The reality is simpler. If you’re sending the same email to a lot of people, you’re a bulk sender, period.”

When it comes to the definition of a bulk sender, the quantity of sent messages may be a guideline, but one thing is not: as soon as you are designated as a bulk sender, that’s a title you just can’t shake. We’ve got a few soothing email mantras for you throughout this post to help wrap your brain around some of the inbox update nuances. Here’s the first:
“Once a bulk sender, always a bulk sender.”
As soon as you reach the point in your sending journey where you are distributing a large volume (in the 5,000-email ballpark), congrats, you’ve joined the bulk senders club and it’s a lifetime membership. From this point forward, you will be held to inbox standards that govern mass sending.
Having senders leverage DMARC not only helps to protect their own brands from being spoofed, but also helps users to really make sure they are getting legitimate emails from a specific brand. DMARC is designed for this type of validation, but it is a bit harder to implement than other standard required authentications like SPF and DKIM.
So, let’s talk about the key difference between DMARC and other authentications, and how it helps mailbox providers crack down on spammers that like to spoof legitimate domains.
“Understanding DMARC policies, what the policy enforcement means, and the reports that come back gets technical. We want to make sure this technical info gets heard because there are some really great resources and companies doing good work around helping people implement DMARC processes, and learn what’s happening with their email programs. You would want to know if someone was out there impersonating your brand in the world, and DMARC covers senders who are worried about that.”

So, what is DMARC? Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an authentication method designed to stop bad actors from impersonating you. Basically, it’s just a line of code that goes into your DNS TXT record, and you (the sender) have the option to set a policy within, (p=none, p=quarantine, or p=reject). And that policy instructs receiving mail servers what to do with emails that don’t pass validation.
There are three main email authentications, SPF, DKIM, and DMARC. Many senders have yet to adopt DMARC, perhaps because of the extra steps to implement and the more technical nature of the process. Last year, our State of email deliverability report found fewer than half of the senders we surveyed (42.5%) were certain DMARC was being used for authentication.
DMARC depends on SPF and DKIM to help authenticate messages but takes it a step further and tells receiving servers how to handle messages that fail authentication. That’s the missing piece that will help mailbox providers clean more spammers out of the inbox.
We’ll use ourselves as an example. Here at Sinch Mailgun, our Acceptable Use Policy already requires that senders using the platform adhere to a 0.08% spam complaint rate maximum. That’s because we want to make sure spammers aren’t using Mailgun Send, and we need to protect the reputation of our senders using shared IPs.
A quick Google search reveals 0.1% is a standard benchmark for a healthy spam complaint rate. A 0.1% spam rate means that 1 person has marked you as spam out of 1,000 messages sent. So why are Yahoo and Gmail coming in at 0.3% with these requirements?
“We chose 0.3% because there are other companies and programs out there and 0.3% or below is the requirement for them already. If your traffic sustains a spam rate above 0.3%, you’re probably already in a world of hurt. Generally, we look for much smaller numbers, but 0.3% resonates with the industry so we chose to make it public.”

The industry has always looked at spam rates as an indicator of a reliable bulk sender, but now that it carries more weight, here’s another mantra for you:
“More than a day, less than a year.”
If you hit a peak complaint percentage for some reason on a campaign it won’t necessarily be held against you. Maybe you made a mistake on the sender side or wrote a spammy subject line. Maybe a few more recipients than normal marked your message as spam. Whatever the reason, mailbox providers will look at your rate over a “reasonable amount of time”, weeks – months even, to see what the average volume is. Consistently hold a poor spam rate and it will impact you. But infrequent offenders experiencing outlying issues won’t be docked.
Many senders already include an unsubscribe link in the footer copy of their emails, a standard practice and a default setting if you’re using any kind of email template. This type of unsubscribe link is not the 1-click unsubscribe process these updates require. What is required is that senders put list-unsubscribe post headers into the header of their email as specified by RFC 8058.
If that sounded like some Top Gun mission gibberish to you, you’re not alone. The 1-click unsubscribe portion of these requirements has stimulated a lot of questions from senders across the board. Here’s what it means, and why it matters.
If you’re sending an email to an inbox provider like Yahoo or Gmail, or an email application that can understand the RFC 8058 standard, the user will see an unsubscribe option above the message within the UI of the email application.
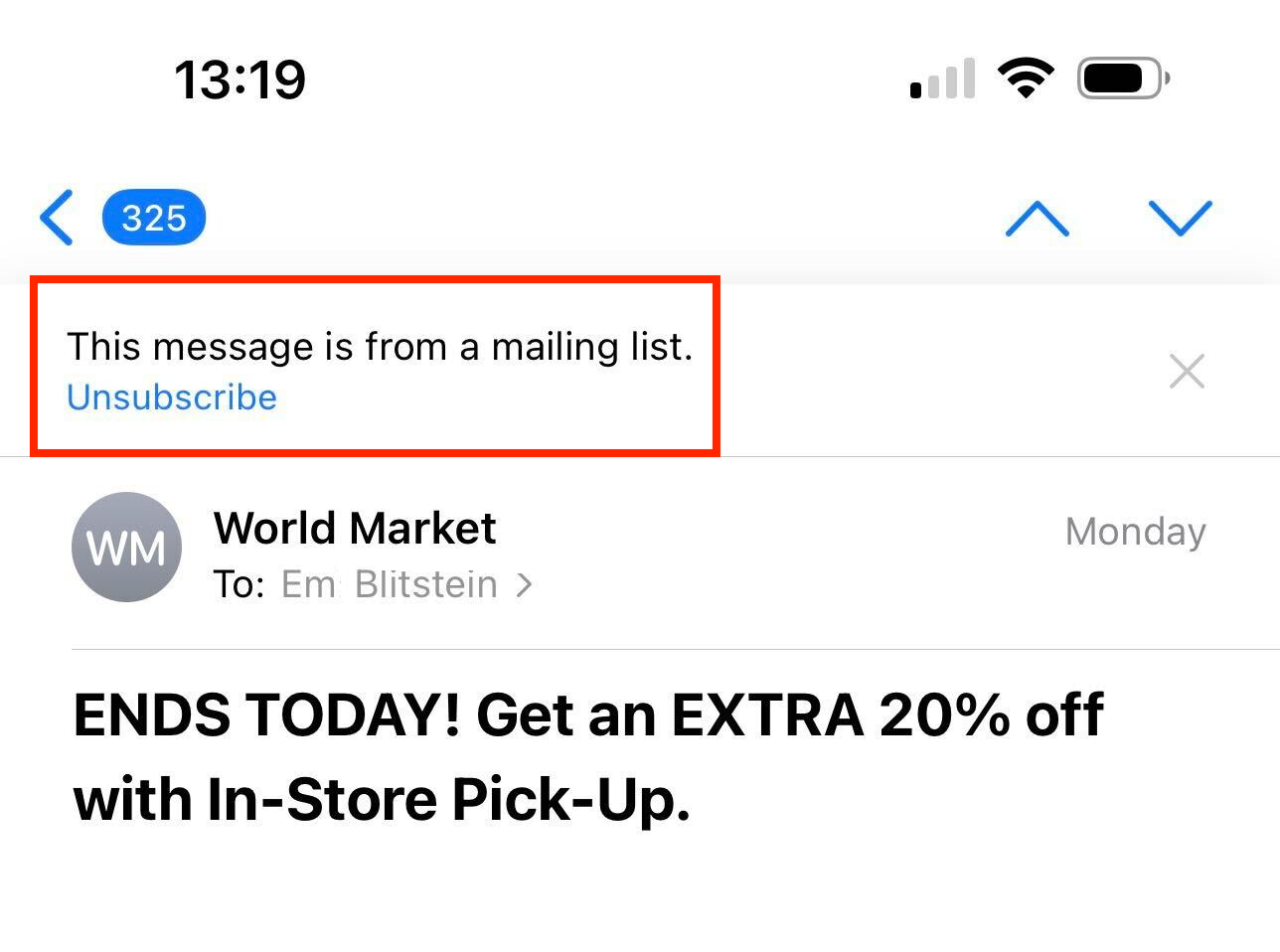
When the user clicks on the unsubscribe link via the provider’s UI, the ISP completes the unsubscribe process for them. Then, the sender is responsible for processing the unsubscribe data and updating their email list within 48 hours of the unsubscribe action. So how does this help you as a sender? The answer goes back to user experience and making things easier for the user.
It’s a lot more likely that a user will unsubscribe to a message if it’s visible from within the UI, rather than opening an email, scrolling all the way to the bottom, clicking an unsubscribe link, confirming their email, and on and on. Many users won’t stick around for that many steps and are more likely to mark unwanted messages as spam just because it’s an easier process.
“We want users to unsubscribe to messages they don’t want; we don’t want them to mark them as spam and hurt the reputation of the sender. We have seen by implementing this unsubscribe affordance in the UI that spam marks go down and in some cases are being reduced by 30 to 40%.”

Now that we’ve covered the basics of the announced inbox requirements, one of the first things some senders might do is try to find a way out of it all. We get it. It sounds intimidating and time consuming to implement DMARC and adopt the RFC 8058 standard, all while keeping your spam complaint rate below 0.3%. You may even be thinking that there are ways around being seen as a bulk sender, and therefore escaping these requirements altogether, but this is not a red pill, blue pill situation.
This is the internet, and there are always shortcuts. When it comes to the inbox updates, industry leaders suggest that you think twice before slinking through a back door. If you are a rule challenger or looking for secret tunnels and loopholes to get around these requirements, don’t.
There are a couple classic ways that scammers traditionally get around sending limits, or practices they employ to stay under the radar and disguise themselves as small volume senders. Here are a couple of big ones that you might be doing (or are tempted to try) without realizing it’s spammy behavior that will tank your reputation.
Using a lot of different IP addresses to spread out the load so you’re staying well under the bulk sender limit per IP. Even if you get clever like a spammer and hide your IP (using a tunneled connection), ISPs have many methods of detecting and identifying this type of behavior.
Using different email addresses from the same domain to send to a lot of other people directly, or by using the CC, BCC fields. Essentially this is delegated flier distribution. If you’re sending 1,000 emails from 10 different addresses on the same domain, you’re still sending 10,000 emails from that domain, and that makes you a bulk sender.
We’ve said it a few times throughout this post, but these requirements are not new standards. Every element of these updates has been a recommended practice for years, and many senders have already implemented these requirements. So why is this enforcement happening now?
“You can get very philosophical about why now. I remember talking about these changes 10 years ago with a group and we said ‘no auth, no entry’, that is what we should be working towards because it makes a ton of sense being able to identify who is sending an email. It helps us assign your reputation to your identity. Email volume keeps increasing and there is a lot of noise and a lot of bad actors piggybacking on sender’s good reputations. At some point on the mailbox provider side, we just had to say okay, that’s enough.”

The goal is to make the inbox a better, safer experience for users. And remember, these users are shared customers between senders and mailbox providers. These requirements not only help protect inbox users from spammers and unwanted mail, but make it easier for mailbox providers to support reputable senders – if those senders can all adopt these requirements to make it easier to mailbox providers to manage inboxes.
We’re fighting back the urge to sing Circle of Life.
If implementing these changes and even just checking your email program to see if you’re meeting the requirements sounds daunting, that’s ok. In fact, it’s been a common response since these requirements were announced. You don’t have to figure it out by yourself. Sinch Mailgun is proud to provide our users with deliverability experts like Jonathan Torres and his team. These guys eat deliverability issues for breakfast.
If you’re looking for more information on the Gmail and Yahoo inbox changes check out these resources, including our fireside chat webinar with Gmail and Yahoo, or reach out to our deliverability pros for some personalized insights.