Deliverability
Beware of phishing emails
Deliverability

NOTE: If you suspect you have received a phishing email impersonating Mailgun, please send the email headers to abuse@mailgun.com.
You’ve got mail!
But is it legitimate?
Even if you recognize the company that sent you the email, it’s best to double-check any emails that request sensitive information, like password resets or billing details. After all, the email could be a sophisticated phishing attempt or malware attack from a cybercriminal.
Let’s go over what phishing emails are, how to recognize them, and steps to protect yourself from phishing scams.
Phishing scams are emails that pretend to be legitimate businesses to gain your personal information. These emails include links leading to a landing page asking you to input sensitive information like your password, bank account number, phone number, credit card number, or social security number.
In other cases, scammers include email attachments that, when opened, infect your device with malware. Phishing is the internet version of social engineering.
Cybercriminals use phishing messages to:
Sinch’s 2025 report, The state of customer communications, found that nearly half (48%) of consumers received a phishing email in the past year, and 28% admitted they clicked on a suspicious link at least once. Those odds mean you can’t rely on recognition alone when judging an email’s legitimacy.
Okay, so it sounds pretty scary. Before we go over how to protect yourself from phishing attempts, let’s look at some common types of phishing emails, as follows:
We’ll dig into three of these examples in more detail below.
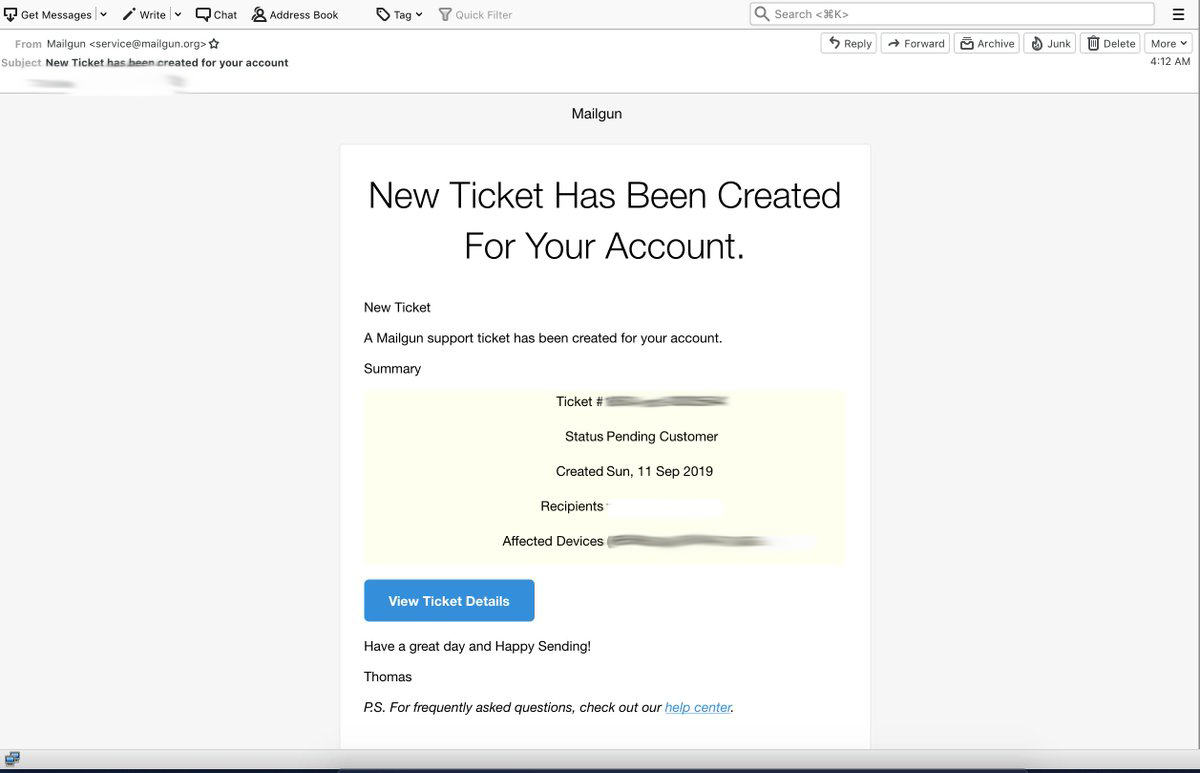
The Login Scam collects your username and password. We’ve seen it recently at Mailgun. Take a look at the message below.
Looks legitimate, right? But wait, it gets worse. This is the landing page the phishing email sends you to if you click the link:
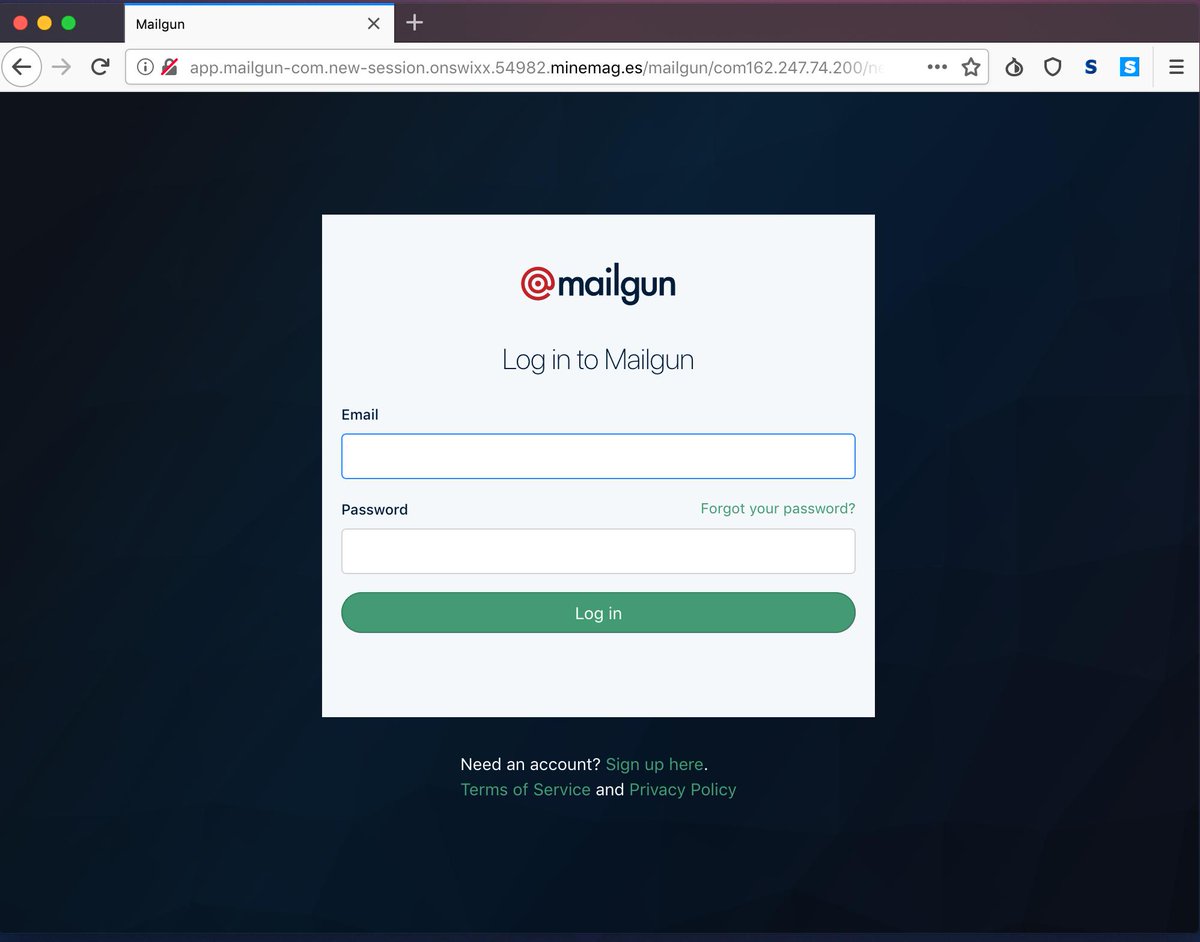
We were almost fooled, too, but this is not the Mailgun website. If you input your login details in the fake website above, the cybercriminal can collect your credentials and lock you out of your account in seconds.
The Fake Invoice Scam relies on fear and urgency to pressure you to submit a payment for goods or services that you never ordered. For instance, you might be told that there are serious repercussions if you don’t pay your outstanding invoice within one or two days.
The Google Docs scam involves an email that appears to be from someone you know, like a colleague or friend. Once you click on the link to open the “Google Doc,” you’ll be taken to an almost identical version of Gmail’s login page. With this fake landing page, cybercriminals can steal your Google account details.
A few years ago, phishing attempts always looked like any other spam email with their bad grammar, broken email templates, and outdated logos. Then, scammers learned that they need to be craftier and create more convincing phishing emails.
If the spammer is really committed to their scam, they’ll do what it takes to make the email they send you look legitimate, like the fake Mailgun email shown above. The formatting on the email is a little off, but the biggest sign that jumps out to us is the from address, service@mailgun.org. That’s not a legitimate Mailgun address.
Below, we’ll go over some ways to recognize sophisticated phishing scams, including:
When checking if you’ve received a phishing attempt, look at the message headers. These headers will give you every single last detail of a message – including who and where it’s coming from in the first place.
To find the headers on various email clients:
You can also use tools like MXToolBox to parse message headers for you. If the email in question doesn’t have the right authentications in place, like its SPF, DKIM, or DMARC, then it isn’t coming from the sender it claims to be.
Check the URL of the landing page that the email redirects you to. This one is usually a dead giveaway.
The example above is a bit tricky because the beginning of the URL looks pretty legitimate. It tries to trick you with the mailgun-com, hoping that your eyes will gloss over the fact that it isn’t our website. If that isn’t enough, the rest of the URL is just as bogus. Always double-check a URL when you receive a message asking for personal information.
Is your email addressed to you, or is it a generic greeting like “Hello Sir or Madam”? If a legitimate email asks for personal details, it’ll probably address you personally. If you spot this detail, double-check for other red flags to see if your email is a phishing attempt or legitimate.
Most banking services and other legitimate businesses will never ask you to share your personal details or financial information unprompted. If you’re asked for personal information, verify that the email sender is legitimate.
In general, it’s good practice to scan all attachments for malware. But, if you’re receiving a suspicious email from a questionable sender with an attachment, it’s best to check if the message is a fraudulent email first. Chances are, the attachment is a vehicle for ransomware to hitch a ride to your device.
We’ve gone over some typical phishing scams and how to recognize them. Here are some best practices to protect yourself from these attacks:
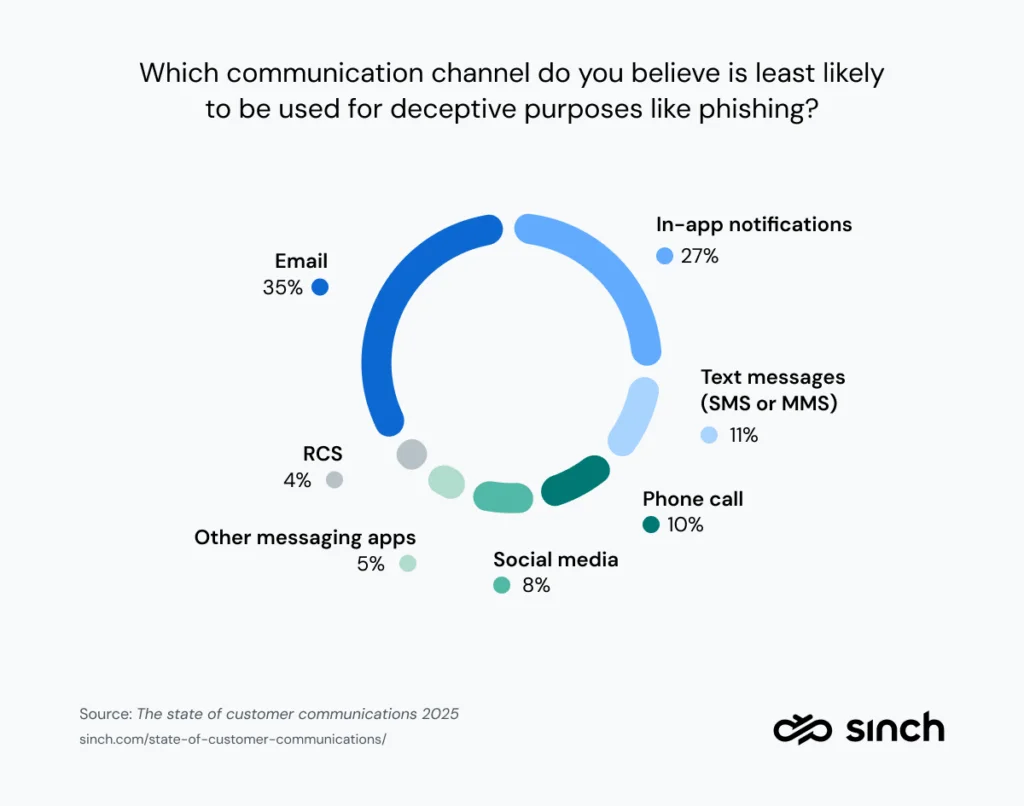
Always keep your guard up. Even if you think you know how to stay safe, hackers will exploit that false sense of security. In fact, 35% of people in the 2025 State of customer communications report said they believe email is the least likely channel for phishing, even though it remains the most popular attack vector – with billions of fake emails sent every day. That perception gap leaves many people more vulnerable than they realize.
Outside of being vigilant about phishing attempts, there are some added steps you can take to keep yourself and your data protected:
If you think you’ve received a phishing email:
Instead, we recommend taking these steps:
Should you suspect that you’ve received phishing attempts that look like they’re coming from Mailgun, please send your message headers to abuse@mailgun.com. We’ll take it from there.
And that’s it! We hope these tips and tricks will keep you phishing-free and safe from cybersecurity risks.
Remember to always investigate emails that land in your inbox. Education is key to preventing cybercrime, so take any opportunity you have to share this knowledge with others in your team. We’re in this together.
Here at Mailgun, we take pride in our industry-leading approach to email security. We adopt a multi-faceted community approach to keep our users safe. With the help of the wider security research community, we stay ahead of malicious phishers as their efforts become more sophisticated.
Ready to get sending? Check out our Mailgun service for free today.